
API Management
Harness API Management to accelerate development,
unlock innovation, and strengthen data governance
Held back by your integration strategy?
Jade has been building and supporting enterprise scale software solutions for more than 30 years. The complexity of architectures has dramatically evolved, as companies adopt new SaaS solutions to complement their custom-built core systems.
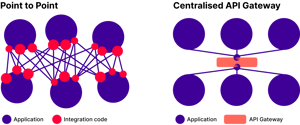
Many companies struggle to ensure their integration strategy keeps pace with this ever changing landscape. Traditional, decentralised, point-to-point integrations can create a tangle of dependencies.
For companies with complex integrations, when things do go wrong it can be much more difficult to pinpoint the cause increasing the likelihood of extended service disruptions.
Tightly coupled integrations increase the cost and risk of change as impacts cascade across connected systems, reducing agility and innovation.
The absence of centralised policies relating to security, authentication and encryption risks non-compliance with data management and protection regulations.
The solution
Design
An overall API strategy and architecture defines a comprehensive set of principles and policies covering areas of security & encryption, version control & deployment, monitoring & analytics, scalability & reliability. This ensures all future work is undertaken to ensure a sustainable, efficient and complaint solution.
Implement
A discoverable catalogue of APIs tailored to business domains and individual use cases. Each API contains automated tests and is supported by comprehensive documentation and version control. This approach saves time and reduces friction when creating new products and services.
Optimise
Jade's monitoring, support and maintenance services guarantee the ongoing performance and availability of business-critical integrations. Analytics and reporting provide insights into patterns of API usage that can inform business decisions and support further optimisation.
Benefits
Between internal teams and partners through the reuse of discoverable assets to reduce cost and accelerate the pace of change
By centralising policies for authentication, authorization, and encryption, reducing exposure to cyber-attacks and data breaches
By seamlessly integrating legacy systems with new technologies such AI, to create responsive, cross-platform user interactions